MAIN MENU MOVED TO THE BOTTOM OF THE BLOG!
Search This Blog
Friday, August 31, 2012
Go Google: Google Drive
Published on Apr 24, 2012 by Google ; Introducing the all-new Google Drive. Now access your files, even the big ones, from wherever you are. Share them with whomever you want, and edit them together in real time.
Thursday, August 30, 2012
State approves Facebook’s plan to issue stock for Instagram purchase
 The state of California today approved Facebook’s plan to acquire Instagram for $300 million in cash and 23 million shares of its stock. This brings the deal, which was announced in April, closer to closing. Instagram shareholders still have to vote to formally approve the sale.
The state of California today approved Facebook’s plan to acquire Instagram for $300 million in cash and 23 million shares of its stock. This brings the deal, which was announced in April, closer to closing. Instagram shareholders still have to vote to formally approve the sale.
This morning lawyers and employees from Facebook and Instagram attended a “fairness hearing” before the California Department of Corporations. Facebook called for the hearing as a way to obtain exemption from federal registration and speed up the acquisition process. Without a state-level fairness hearing, it can take more than six months and over $250,000 to register a securities offering, according to the California Department of Corporations website. California is one of six states in the U.S. that allow this quicker and more cost-effective review.
Since the time Facebook announced its intent to buy Instagram, its shares have lost significant value on the public market. The formerly $1-billion deal is now worth close to $750 million at Facebook’s $19.10 share price as of today at 1 p.m. PT. The LA Times reports that co-founder and CEO Kevin Systrom says he recognized the risk of Facebook losing value and was negotiating on the basis of cash and stock options, not the end valuation. He says the media played up the $1-billion valuation, but he believes Instagram’s 19 shareholders will still vote in favor of the deal.
“We still believe firmly in the long-term value of Facebook,” he said.
Systrom also revealed that although he had been approached by other companies looking to buy Instagram, no formal offers had been made.
Last week, the Federal Trade Commission closed its investigation of the acquisition without taking any action, allow the deal to proceed. Instagram has gained more than 50 million new users in the four and a half months since Facebook announced its plans to acquire the mobile photo-sharing network.
Source here >>
Monday, August 27, 2012
A fast-growing trend among adult women : social bookmarking
Published on Aug 27, 2012 by ABCNews : Pinterest, A Social Bookmarking Website, Skyrockets in Popularity among adult women.
India censors social media after riots
Published on Aug 24, 2012 by AlJazeeraEnglish : The Indian government has called on social media websites like Twitter and Facebook to remove what it calls objectionable content after sectarian violence broke out in the state of Assam. Last week the authorities blamed groups in Pakistan for circulating hate videos showing attacks against Muslims, but among the sites banned are news agencies covering the violence.
Winner and losers from the Samsung Apple clash
Published on Aug 27, 2012 by Euronews : Samsung's big loss to Apple in a potentially game changing US patent lawsuit over smartphones meant a dramatic fall in the South Korean company's shares in Soeul - down almost 7.5 percent - while Apple's stock rose in New York on Monday.
But the industry is still sorting out who will be the long term winners and losers in the smartphone world.
Google may suffer as it supplies the Android operating system for Samsung phones. That means it could lose out if Apple manages to get permanent bans on the sale of some Samsung handsets.
A decision on that is due from the court next week.
Partially blocking Samsung from the US market could dramatically change the league table where the South Koreans dominate with 32.6 percent of all smartphone sales worldwide between April and June. Apple had 16.9 percent, Nokia 6.6 percent, Taiwan's HTC 5.7 percent and China's ZTE had 5.5 percent.
Investors obviously think Nokia could be a winner from Samsung's setback.
The Finnish firm's shares shot up on Monday. Its newest smartphones use a Microsoft operating system, which Apple has no problems with.
Other handset makers will now be worrying whether they will be next on Apple's litigation list and how much this case will change the dynamics of the highly competitive mobile phone industry.
Sunday, August 26, 2012
Samsung bites back after Apple victory
Published on Aug 26, 2012 by AlJazeeraEnglish : South Korean technology giant Samsung says consumers will now face fewer choices, less innovation and higher prices. That is after a US jury ordered the company to pay more than one billion dollars to Apple for stealing its technology. It is only one of the many international legal battles between the two, all of which could change the industry.
IP- a threat to knowledge for human benefit & free market?
Samsung ordered to pay Apple $1bn
Published on Aug 24, 2012 by AlJazeeraEnglish : A California jury has found that Samsung, the Korean electronics giant, deliberately copied elements of Apple's iOS-based product line.
The jury ruled that Samsung willfully infringed at least three of Cupertino-based Apple's patents, including navigation, zoom features and icons.
US brought cyber war to Afghanistan: general

USMC Lt. Gen. Richard Mills speaks during a ceremony in Avondale, La., July 28, 2012.
The US military has been conducting cyber-attacks against its perceived opponents in Afghanistan, according to one of its generals.
Marine Corps Lieutenant General Richard Mills made the unusually explicit acknowledgment at a conference in Baltimore last week, The Associated Press reported on Friday.
Mills was in command of US-led foreign forces in southwestern Afghanistan between 2010 and 2011.
At the conference, he explained how US commanders regard cyber weapons as an important part of their arsenal.
“I can tell you that as a commander in Afghanistan in the year 2010, I was able to use my cyber operations against my adversary with great impact,” he said.
“I was able to get inside his nets, infect his command-and-control, and in fact defend myself against his almost constant incursions to get inside my wire, to affect my operations,” he added.
There’s been no immediate comment so far from the Pentagon on Mills' speech.
The US has been accused of conducting cyber warfare in many countries in the Middle East and North Africa.
A recent book by New York Times reporter David Sanger recounts how US President Barack Obama ordered a wave of electronic incursions to sabotage Iran's nuclear energy program.
The US-led war in Afghanistan began in 2001. The offensive removed the Taliban from power, but insecurity continues to rise across the country, despite the presence of about 130,000 of US-led troops.
Saturday, August 25, 2012
The Rise of Cross-Platform Malware
For most of the recorded history of malware, viruses, Trojans and other malicious software have been specialists. Each piece of malware typically targeted one platform, be it Windows, OS X or now, one of the mobile platforms. But the last few months have seen the rise of cross-platform malware that have the ability to infect several different kinds of machines with small variations to their code.
Attackers, like people in other walks of life, tend to specialize. They find something that they're good at, say, writing Windows rootkits or creating OS X Trojans, and they often will stick with that. There's not much reason to branch out if they're having success with something already. For a long time, most malware was written for Windows, because that's where most of the users are. Going after OS X or Linux didn't make a lot of sense.
But that's begun to change lately. One recent example is the Crisis Trojan, which has the ability to infect both Windows and Mac OS X machines. The first version of Crisis that researchers discovered targeted various versions of OS X, and it was a typical data-stealing Trojan, listening in on email and instant messenger communications. The interesting thing about Crisis is not only that there are versions for multiple platforms, but also that the installer for the malware, which masquerades as an Adobe Flash installer, checks to see what operating system it's on and then installs the appropriate version.
The malware also has a function that looks for VMWare images stored on the infected machine, and if it finds one, it will mount the image and then copy itself to the virtual machine image.
Researchers found a similar piece of malware back in April. That one was disguised as a Java applet that would install different payloads depending upon what OS the target machine was running. So, attackers have decided that more is better when it comes to platforms. Why restrict your creation to just Windows or OS X when you can have both?
Microsoft researchers looked at a recent attack that involved a piece of malware using similar techniques and found that the attackers have been honing their skills.
Read more >>
Friday, August 24, 2012
There's no escaping the mobile-ad
Published on Aug 23, 2012 by CNETTV Update : YouTube searches for more money, Google+ adds features that can annoy, and Microsoft gets a design makeover.
Thursday, August 23, 2012
Microsoft Unveils a New Look
In advance of one of the most significant waves of product launches in Microsoft’s history, today we are unveiling a new logo for the company.

It’s been 25 years since we’ve updated the Microsoft logo and now is the perfect time for a change. This is an incredibly exciting year for Microsoft as we prepare to release new versions of nearly all of our products. From Windows 8 to Windows Phone 8 to Xbox services to the next version of Office, you will see a common look and feel across these products providing a familiar and seamless experience on PCs, phones, tablets and TVs. This wave of new releases is not only a reimagining of our most popular products, but also represents a new era for Microsoft, so our logo should evolve to visually accentuate this new beginning.
The Microsoft brand is about much more than logos or product names. We are lucky to play a role in the lives of more than a billion people every day. The ways people experience our products are our most important “brand impressions”. That’s why the new Microsoft logo takes its inspiration from our product design principles while drawing upon the heritage of our brand values, fonts and colors.
read more >>
read more >>
Apple-Samsung Patent Case : Consumers the real losers?
Published on Aug 22, 2012 by AssociatedPress : Jurors began deliberating Wednesday in a multibillion dollar patent infringement case pitting Apple against Samsung over the design of iPhones and iPads, but few experts were expecting a quick verdict. (Aug. 22)
Shamoon the Malware in Aramco Attack?
While researchers continue to dig into the Shamoon malware, looking for its origins and a complete understanding of its capabilities, a group calling itself the Cutting Sword of Justice is claiming responsibility for an attack on the massive Saudi oil company Aramco, which some experts believe employed Shamoon to destroy data on thousands of machines.
The attack on Aramco occurred on August 15, taking the main Web site of Saudi Aramco offline. Officials at the company said that the attack affected some of the company's workstations, but did not have any effect on oil production or on the main Aramco networks. The attackers claiming responsibility for the incident dispute that, saying that they deployed a destructive piece of malware that erased data on infected machines and then made them unusable.
"As previously said by hackers, about 30000 (30k) of clients and servers in the company were completely destroyed. Symantec, McAfee and Kaspersky wrote a detail analysis about the virus, good job. Hackers published the range of internal clients IPs which were found in the internal network and became one of the phases of the attack target," the group said in a post on Pastebin shortly after the attack.
The first indications that the attack might be connected to the Shamoon malware came in the group's original Pastebin post, which included a start time for the attack on Aramco, 11:08 a.m. local time in Saudi Arabia on August 15. Researchers who dissected Shamoon found that the same time was hard-coded into the Shamoon malwareas a kind of checkpoint. The attackers claiming responsibility for the operation said that the attack ended a few hours after it began, but that plenty of damage was done.
- "In the first step, an action was performed against Aramco company, as the largest financial source for Al-Saud regime. In this step, we penetrated a system of Aramco company by using the hacked systems in several countries and then sended a malicious virus to destroy thirty thousand computers networked in this company. The destruction operations began on Wednesday, Aug 15, 2012 at 11:08 AM (Local time in Saudi Arabia) and will be completed within a few hours," the post says.read more >>
Sunday, August 19, 2012
Facebook returns to No. 2 spot among U.S. video sites
beating Yahoo, Vevo | 17 Aug 2012
Facebook is once again the second largest video site in the U.S., according to ComScore.
The social network saw 53 million unique video viewers in July. That’s about a third of Google’s audience, but higher than the number of unique viewers on Yahoo sites and Vevo, both of which were ahead of Facebook in May.
Although Facebook’s viewers are up from 44 million in May, average minutes watched per user is down from 27 to 21.7. That’s fewer minutes per viewer than any other site in the top 10 besides Amazon. Google sites, by comparison, averaged about 525 minutes per viewer. However, ComScore’s data only looks at U.S. video views, so Facebook’s global reach is not reflected in the chart below.
 With YouTube, Google still dominates the U.S. web video space, but Facebook could possibly capitalize on its own reach if it ever pushed more in that direction. It seems the social network is heavily focused on photos first, but a number of video sites and apps, including Vevo, Socialcam, Viddy and Chill, have seen positive results from integrating Facebook Open Graph.
With advertisers constantly pushing for new ad formats, we wonder whether Facebook might introduce more video advertising opportunities. With the page post ads now being tested in News Feed, advertisers have more prominent ad space than ever. We could see some companies, particularly movie studios, pushing video ads in this spot.
Among online video ad properties measured by ComScore, Facebook doesn’t even rank. Google, Hulu and a number of video ad networks and exchanges make up the top properties in terms of total ads and minutes viewed.
read more >>
With YouTube, Google still dominates the U.S. web video space, but Facebook could possibly capitalize on its own reach if it ever pushed more in that direction. It seems the social network is heavily focused on photos first, but a number of video sites and apps, including Vevo, Socialcam, Viddy and Chill, have seen positive results from integrating Facebook Open Graph.
With advertisers constantly pushing for new ad formats, we wonder whether Facebook might introduce more video advertising opportunities. With the page post ads now being tested in News Feed, advertisers have more prominent ad space than ever. We could see some companies, particularly movie studios, pushing video ads in this spot.
Among online video ad properties measured by ComScore, Facebook doesn’t even rank. Google, Hulu and a number of video ad networks and exchanges make up the top properties in terms of total ads and minutes viewed.
read more >>

Thursday, August 16, 2012
Two new social sites launched – Medium and Branch

Twitter founders Evan Williams and Biz Stone have launched two new social networking sites, Branch and Medium Photograph: Jeff Chiu/AP
They inspired a boom in self-publishing with Blogger, then turned the world to 140 characters with Twitter. Now Ev Williams and Biz Stone have launched two new websites – Medium and Branch – in what they hope will prompt an "evolutionary leap" in online sharing.
Williams and Stone are still directors of Twitter, but are involved in the new ventures through their San Francisco-based incubator fund, The Obvious Corporation.
Like Twitter, both Medium and Branch are publishing platforms where users can share pictures, articles and text. And both are more or less splinter services to Twitter.
But what are Medium and Branch?
Medium
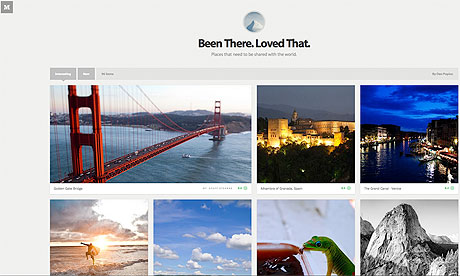
Medium is built around collections. For now Medium is invite-only, but soon anyone will be able to start a collection and publish their own photographs or writing.
Read more >>
Read more >>
Tuesday, August 14, 2012
Password Dos and Don’ts
 There’s a saying when it comes to online passwords: they’re like a toothbrush. That’s because you want a good toothbrush (just like a password), you should change it often (just like a password) and you should never share it (just like a password!).
There’s a saying when it comes to online passwords: they’re like a toothbrush. That’s because you want a good toothbrush (just like a password), you should change it often (just like a password) and you should never share it (just like a password!).
There are some key dos and don’ts that can help:
DON’T
- use personal information that could be easily guessed or accessed, like your birthday (which happens more often than you might think) — it’s easy for you to remember, but easy for someone shady to find
- use actual words that you can find in actual language (any language)
- use the same password for all of your accounts
DO
- use a different password for each account
- combine capital letters, numbers and special characters
- change your password once every three months or so — and immediately if a site notifies you of a security breach
- use the Master Password feature in Firefox (more on that here.)
By now you’re probably thinking, “I can’t remember my keys in the morning. How am I supposed to remember all these new passwords all the time?”
Here are a few steps to creating easy-to-remember passwords that are still secure.
- Choose a phrase — let’s try “The quick brown fox jumps over the lazy dog.”
- Use the first letter in each word and capitalize the first one: Tqbfjotld
- Make it stronger by adding a special character: Tqbfjotld!
- Now, associate it with each website you log in to. For example, you could use YT for YouTube, FB for Facebook, your bank’s initials — you get the point. So your password would now look like this:
YTTqbfjotld! (for YouTube)
FBTqbfjotld! (for Facebook)
and so on, and so on…
Choosing secure passwords will go a long way to keeping you safe online.
Original here | 7 Aug 2012
The ABCs of Apple v. Samsung
There are five drama-laden days of hearings coming up this week in the patent battle between the two tech titans. Here are some bite-sized takeaways to help keep you in the know.
To casual observers, patent disputes too often prove impenetrable -- with their arcane legal arguments and mind-numbing technical detail.
We've seen lawyers snapping at the judge. One of Samsung's lawyers literally begged the court to reverse a ruling. A steady stream of juicy trade secrets has flowed out of both companies in the form of courtroom exhibits. And somewhere just offstage waits a third powerful player.
CNET broke the news last week that Google, the company that isn't a party to the suit but has plenty at stake, is lending aid to Samsung as well as other Android partners that Apple has named in similar patent suits.
Related posts
Trust us, as we go into a full week of new courtroom testimony, there's still plenty of action left. Here are some key facts to help you stay on top of it all.
How did this start? You can trace the clash back to January 9, 2007, when the iPhone debuted. Apple said in a lawsuit it filed against Samsung in April 2011 that within a couple of years of Apple's releasing the iPhone, Samsung had created iPhone clones that ripped off Apple's technology and designs. Apple also claims Samsung did the same thing after the iPad came out. Samsung responded by countersuing Apple for patent infringement.
What's at stake? Apple wants $2.5 billion if it wins. Samsung is also seeking monetary damages. What this case is really about, though, is stopping Google and its Android operating system. Steve Jobs, the late Apple co-founder and CEO, said before dying last October that he wanted to destroy Android because he considered it a "wholesale" ripoff of the iPhone.
If Apple wins, the company's lawyers will first be able to force Samsung to stop shipping some of its handsets and computer tablets in the United States but more importantly, Apple will have a nice precedent with which to attack HTC and other companies that use Android. If Apple loses, then the decision will obviously work against Apple's larger anti-Android strategy.
Why doesn't Apple sue Google?: One likely reason is that Android is free and Google doesn't profit directly from sharing the OS with phone makers. Samsung, on the other hand, chooses to use Android and is generating revenue upon which Apple can calculate damages.
Samsung also makes for an easier target. Apple can compare the iPhone with Samsung's handsets side by side.
Some of the more compelling evidence that Apple has shown to the jury includes side-by-side comparisons of the two company's icons and graphics. Apple has also presented internal e-mails and documents that show Samsung closely studied the iPhone and knew that its own handsets were inferior to Apple's. Apple argues that these documents prove Samsung was trying to mimic the iPhone.Has Apple landed any punches? Apple seems to have the edge when it comes to which side the court favors. In June, the presiding judge in the case granted preliminary injunctions against Samsung's Galaxy Tab 10.1 tablet. In addition, Samsung has received four sanctions mostly related to failure to turn over evidence.
Read Full Report :
Sunday, August 12, 2012
NYPD and Microsoft launch "spying" partnership.
Published on Aug 10, 2012 by PressTVGlobalNews : The new technology partnership between Microsoft and the New York Police department will pair America's largest municipal law enforcement agency with one of the worlds largest developers of computer software and hardware. The mayor of New York has billed the collaboration as a new tool for fighting crime.
Saturday, August 11, 2012
9 Things You Absolutely Must Do to Keep Your Online Identity Secure
We've been reeling a bit ever since Mat Honan was the victim of that ruthless social hack that wiped all his devices. Sure, that was an extreme case. But it's also one that could happen to anyone, at any time. So we put together a list of the best ways to make sure your internet self—your accounts, your cash, and your information—stays secure.
Fortify Your Passwords
Password strength is vital to your frontline defense. Obviously your password should be a combination of letters and numbers, but don't stop at the bare minimum. Use uppercase letters in random spots. Subsitute numbers for letters. Mash multiple word phrases together. Deliberately misspell those words. Space them out. If you're feeling particularly hardcore, you can just create a random string of characters. In fact, XKCD's excellent comic sums this up in a way more eloqent than any words could.

Oh, and for the love Woz, don't use the same password for everything. Particularly not your most sensitive (read: banking) accounts
All HTTPS, All The Time
Many of the vital online services (Google, Facebook, Twitter, etc.), allow you to only connect to their servers via an HTTPS connection. This will encrypt any stream of data between you and the service, ensuring that anyone using Firesheep or a packet sniffer on a (usually public) Wi-Fi network can't glean your login data. Never work at a coffee shop without it.
Secure Those Security Questions
Just the security questions are a backup doesn't mean you shouldn't put the same thought into them as you password. Use numbers instead of letters. Mash entire phrases together into one word. Deliberately misspell things. Or best of all, Kaspersky Labs expert Dmitry
Bestuzhev explains, don't directly answer the security question at all:
Bestuzhev explains, don't directly answer the security question at all:
- The tips are quite simple but effective. Since all social engineering attacks work based on the information of interest for the victim or the information related to the victim, it's important to provide secret questions with the answers absolutely not related to it.
- For example, for the question "What is the name of your first pet?" I would register an answer like sw3SwuTu
- When I bought my last car... The vendor provided me with a list of secret questions and I had to provide them with the secret answers they registered in their systems. So, instead of providing real answers I provided a password like the [aforementioned] one. They said I was the first customer to do this and they congratulated me.
- ... So, basically the rule is never provide real answers for the secret questions."
Friday, August 10, 2012
Facebook next? FB agrees to tighten its privacy policies
Social network settles dispute with FTC over 'deceptive act' of making confidential information public without consent


The FTC said Facebook, which went public earlier this year, was liable for
'a broad range of deceptive conduct'. Photograph: Handout/Getty Images
Facebook has agreed to tighten its privacy policies after it settled a long-running dispute with the US Federal Trade Commission (FTC).
The social network was accused by the regulator last year of introducing "unfair and deceptive" changes to its privacy policies in 2009, including settings that made users' confidential profile information public without their consent.
Facebook also shared personal information including status updates, geographic location and marital status with advertisers and third-party applications without telling users, the FTC said.
News of the settlement, which ties Facebook to biannual privacy inspections by an independent watchdog for the next 20 years, came just a day after Google was fined a record $22.5m (£14.4m) by the FTC for circumventing privacy protections on Apple's Safari web browser.
The allegations laid bare by the FTC about the two internet giants will heighten concern about the security of peoples' private data in some of the most popular digital destinations. Facebook boasts more than 955 million active monthly users, according to its latest figures. Google controlled two-thirds of the US search market in June and its share is even greater in most European countries, said the metrics firm ComScore.
The FTC said Facebook was liable for "a broad range of deceptive conduct" relating to what it tells users about their private profile information.
The bulk of the charges against Facebook relate to its overhaul of users' privacy settings in November 2010. The FTC said that Facebook failed to tell users that it changed the settings so they could no longer restrict access to their name, profile, picture, gender, friend list, pages, or networks.
"Facebook's failure to adequately disclose these facts, in light of the representation made, constitutes a deceptive act or practice," the FTC said.
The social network also made public users' photos and videos even after their accounts had been deactivated.
The five , commissioners were split over whether to settle the dispute, with three voting in favour, one abstaining, and Commissioner J Thomas Rosch dissenting on the basis that Facebook had denied liability for its actions. He argued that it should at least be required to take the position that it neither confirmed nor denied liability – a position he also argued in dissenting from the 4-1 verdict over Google's fine. Google denied liability to the FTC; it was fined because it was already the subject of a consent order similar to that now tying Facebook.
Original report >>
Original report >>
Google to Pay Millions for Latest Privacy Lapse
Published on Aug 9, 2012 : The Federal Trade Commission says it hopes its record $22.5 million fine against Google will force the Internet search behemoth to pay better attention to its practices. The FTC says Google duped Web surfers who use Apple's Safari browser.
Thursday, August 9, 2012
Hackers Take Down WikiLeaks Website

WikiLeaks, the organization that came to fame by publishing confidential government and financial reports, has been the victim of a hacking that's left its website offline.
The denial of service attacks happened over the course of the week, and at first, WikiLeaks, for some reason, thought the attacks were the caused by either of three things: "1. Olympics cover 2. Upcomng [sic] release. 3. Ongoing Syria, Stratfor releases."
All three were wrong. The attacks were carried out by a hacker collective known as AntiLeaks. In a message posted to Twitter, the group explained why it targeted the rebel news organization:
“We are not doing this to call attention to ourselves. We are young adults, citizens of the United States of America and are deeply concerned about the recent developments with Julian Assange and his attempt at aslyum [sic] in Ecuador."Assange is the head of a new breed of terrorist. We are doing this as a protest against his attempt to escape justice into Ecuador. This would be a catalyst for many more like him to rise up in his place. We will not stop and they will not stop us.”
All of this is pretty ironic when you consider the time the Anonymous hacker group came to WikiLeak's defense earlier this year and attacked a number of financial institutions like PayPal and Bank of America with denial of service attacks.
WikiLeaks is currenlty raising money for more bandwidth and is instructing readers and supporters to head to a mirror site to donate money.
Subscribe to:
Comments (Atom)




